FAQ : IDEAL ADMINISTRATION
Управляйте средами Windows Active Directory и рабочими группами с помощью одной консолиС IDEAL ADMINISTRATION 2026 администрирование Active Directory становится ещё более полным. Проактивное обнаружение, интеллектуальный анализ оповещений с помощью облачного ИИ, поддержка принятия решений и теперь безопасное удалённое управление с RustDesk, всё без агентов, для централизованного, эффективного и полностью контролируемого администрирования. ⬇️ 30-дневная бесплатная версия.
How to remotely manage your Windows client workstations?How to administrate a Windows 7, Windows 8 or Windows 10 (and higher) station remotely? |
What are the prerequisites for administering a Windows 7 / 8 / 10 (and higher) computer? I have to administer a Windows 10 station and when I try to display the computer properties, I obtain a "Connection error" message. What can I do to correct this problem? |
|
Here're some general tips to verify for Windows 7 / 8 / 10 (and higher) computers:
You must have administrative rights/privileges over your domains, workstations and servers of your network. Read more: How to get administrative rights?
The "RemoteRegistry" service must be up and running on the remote computer. You can automatically configure in Automatic start using a GPO: Windows Server 2003 Domain Controller
Windows Server 2008/2012/2016/2019 or Domain Controller
The WMI service must be activated on the client workstations for optimal remote management. Our software uses WMI in particular for the installation and remote start of the takeover service (screen sharing). WMI is also used for the recovery of information such as serial numbers, or the memory capacities of remote stations. See our FAQ: How set up a Remote WMI Connection? Network discovery need to be activated. When Network Discovery is on, the Windows 7 / 8 / 10 (and higher) computer can see other network computers / devices and become also visible to other network computers and to our software. This is in Control Panel, Network and Sharing center, Advanced sharing settings
Check if remote connections are allowed on the remote computer: Control Panel \ Security \ Advanced system settings \ Remote use: Allow remote assistance connections (Remote Assistance) and (Remote Desktop).
File and printer sharing need to be activated on the Windows 7 / 8 / 10 (and higher) computer. This is in Control Panel, Network and Sharing center, Advanced sharing settings
Some Antiviruses see our administration tools as false positives and block their execution on remote workstations. This can for example be counteracted by the impossibility of launching the remote control of a remote station because the copying of files is not authorized by your Antivirus. In this case, you must authorize our programs in your Antivirus, namely: - IA.EXE
- IACMD.EXE
- IACMDSRV.EXE
- TVNVIEWER.EXE
- TVNSERVER.EXE
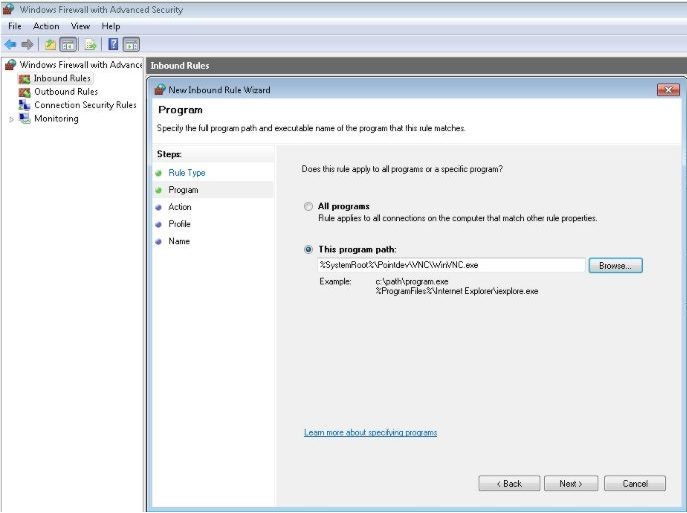
Before administrate a Windows 7 / 8 / 10 (and higher) station, we strongly recommend you first to DEACTIVATE "User Access Control" aka UAC. This is in "Control Panel" ,"User Accounts" , "Turn User Accounts Control on off". To take the remote control of Windows 7 / 8 /10 (and higher) computers with "TightVNC", you'll have to add an exception on the remote computer, into the Windows Firewall for the communication port used by the program (5900 by default) and/or for the program "\Windows\Pointdev\VNC\WinVNC.exe" (VNC Server service) if you use version 1.X of the remote control tool, or for the program "\Windows\Pointdev\VNC\tvnserver.exe" (tvncserver_Pointdev service) if you use version 2.X. The point of creating an inboud rule on the TightVNC program is to not have to modify again this rule if you decide later to change the communication port used by TightVNC. Control Panel -> System And security -> Windows Firewall -> Advanced Settings -> Inbound Rules -> New Rule ... -> Check "Program" Example:
Last, check in the Network Settings if NetBIOS layer is enabled. |
| Также касается следующего программного обеспечения: IDEAL DISPATCH | IDEAL REMOTE | IDEAL MIGRATION |
| Последняя модификация: 25/04/2022 |




IDEAL ADMINISTRATION 26.5.1
БЕСПЛАТНАЯ
ЗАГРУЗКА

 русский
русский 
 Французский
Французский Английский
Английский Испанский
Испанский Немецкий
Немецкий Итальянский
Итальянский