FAQ : IDEAL Alerter
Monitoraggio, avviso e reazione su server e stazioni WindowsCon IDEAL ADMINISTRATION 2026, l’amministrazione di Active Directory diventa ancora più completa. Rilevamento proattivo, analisi intelligente degli avvisi tramite IA Cloud, supporto alle decisioni e ora controllo remoto sicuro con RustDesk, il tutto senza agent, per un’amministrazione centralizzata, efficiente e sotto controllo. ⬇️ Versione gratuita di 30 giorni.
Examples of alertsAudit access to files and directories |
Alert : How to audit access to files or directories ? |
|
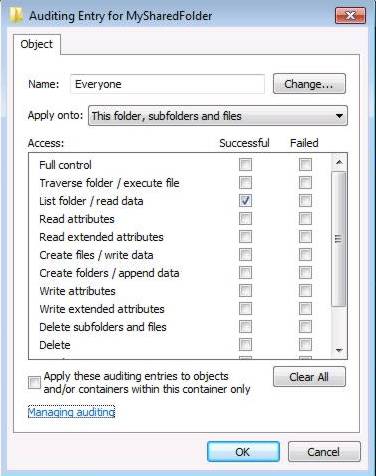
It can be sometimes necessary and judicious to be warned when a user is accessing a shared resource. This example describes the procedure to use in order to audit on a workstation or on a centralized resource (e.g: a file server), all the access of users (read, copy, selection) to a specific file or directory. An email which contains the observation and reaction report will then be sent to warn the administrator. This topic can also be used as a starting point to audit other types of objects (registry key, printer...), for a success, or failure attempts, and this accoring to a group of users, a list of users, or computers. The approach will be then relatively similar. Requirements before creating the alert with IDEAL Alerter :
Check List folder / read data. If the audited object is a directory, it is also possible to apply the observation to sub-objects (files / folders). Then apply the auditing. With IDEAL Alerter :
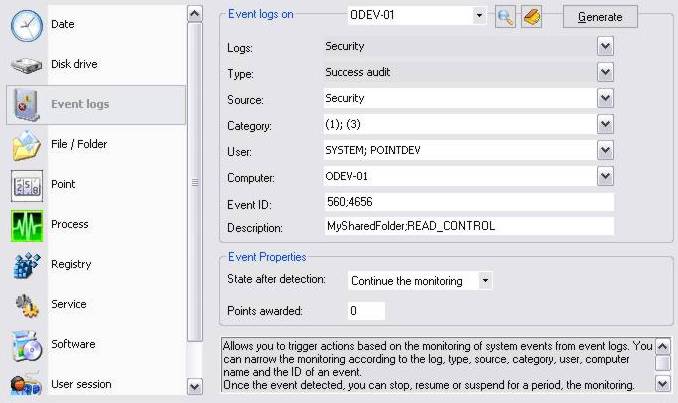
When a user is accessing a file / directory, the event logs generate excessive entries for the same action. Nevertheless, lit is possible to filter the events from their identifier, to keep only accesses on the audited objects. Identifier 560 : Objects access (for 2003 Server, XP computers and previous OS). Identifier 4656 : Objects access (for Vista, 2008 Server, 7 computers). The description "MySharedFolder;READ_CONTROL" identifies here the name of the monitored directory (MySharedFolder) and the access mask to this folder (READ_CONTROL). The state after detection "Continue the observation", enables to infinitely pursue the monitoring of security logs
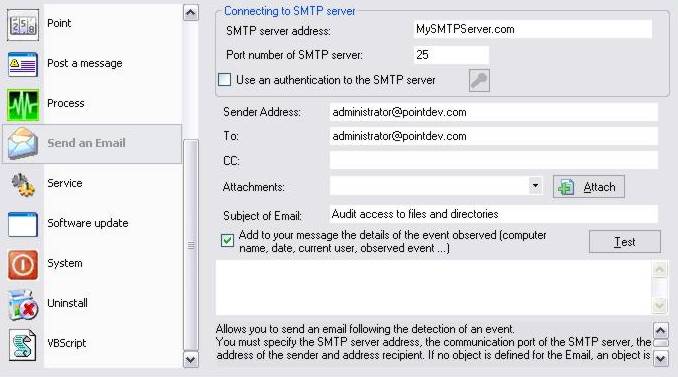
Fill in the different settings required to send the Email.
|
| Ultima modifica: 19/02/2010 |




IDEAL Alerter 2.0

 Italiano
Italiano 
 Francese
Francese Inglese
Inglese Spagnolo
Spagnolo Tedesco
Tedesco Russo
Russo